Network Security
- Project 2
Using IP Security (IPSec) to protect transmitted data
a)
Learning Objectives:
As we have discovered in Project 1, with a protocol
analyzer we can disclose transmitted user data even the user name and password
in authentication phase of some common protocols. In this project, we will use IP
Security (IPSec) protocol set to protect the transmitted data between two
computers running Windows. To test the IP Security configuration we still use
the Ethereal protocol analyzer as in Project 1 and try to read the user name
and password in transmission.
b)
Tools utilized:
-
The IPSec
protocol needs to be configured for this
project.
1.
A Windows server will
serve as one end of the IP Security communication. The server has the following
parameters:
·
The IP address:
192.168.11.50.
·
The testing account
for all services in the server is: username: test/ password: test.
·
The pre-shared key to
be used by the authentication method: dcsl
·
Authentication Header
protocol: MD5
·
Encapsulating Security
Payload protocols: SHA1 and DES
2.
The other end of the IPSec communication will be a student
workstation running the Ethereal protocol analyzer.
·
The student will need
an external hard disk with Windows 2000 professional or windows XP installed.
IPSec support is a built-in function in Windows XP Professional and Windows
2000 Professional.
-
The Ethereal protocol analyzer running on
the student workstation will sniff network traffic traveling between the
workstation and the Windows server.
c)
Requirements:
-
The student must enable
IP Security function in Windows and use it to protect transmitted data from the
client computer to the lab server.
a.
Understand how to
configure IPSec in a Windows system by reading related articles on Microsoft
sites, for example, http://www.microsoft.com/technet/prodtechnol/windows2000serv/howto/ispstep.mspx#EIAA.
b.
Use Microsoft Management
Console (MMC) to configure IPSec on your Windows workstation. Some sample
screenshots of how to use MMC:
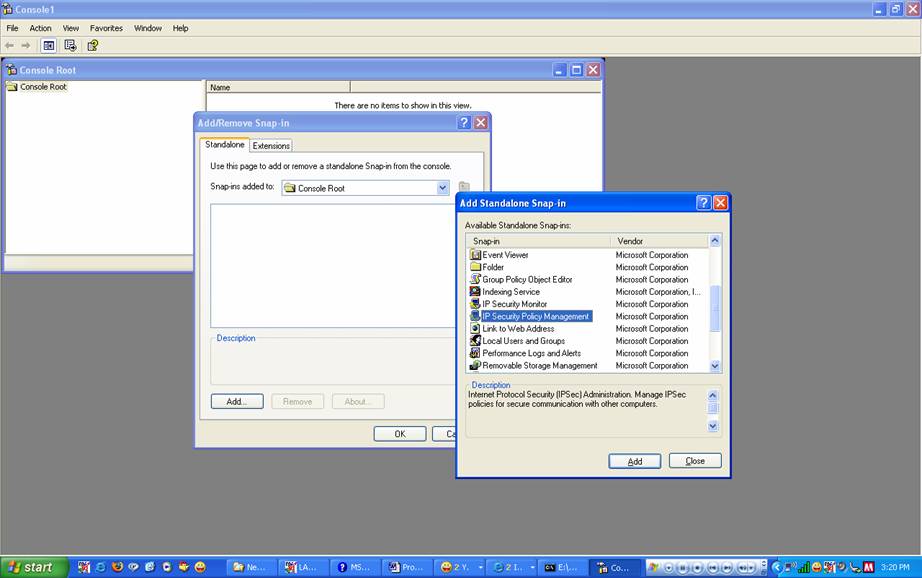
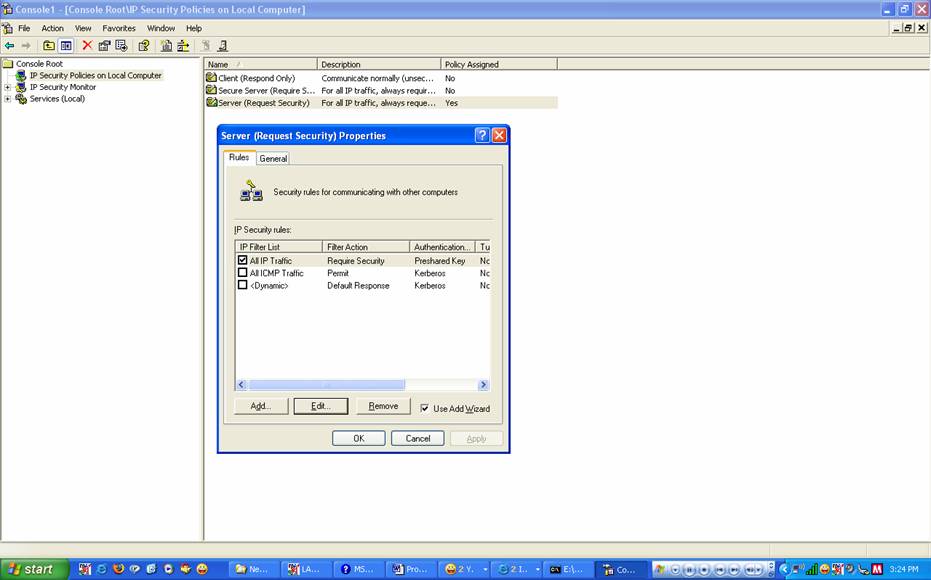
-
The student will use
the ping command in console window
to show the negotiation phase of IP Security. If the IPSec is configured
properly between the two ends, the IPSec negotiation message will be displayed
as part of the ping command output. The
screen shots must be submitted as part of this project.
-
The student will test
the configuration according to the following 3 scenarios. The captured data
must be saved in files as a supplement to the project report.
1.
HTTP traffic:
·
The student will run
the Ethereal against one of the network interface cards.
·
The student will use a
browser to connect to the Web server (as specified in project 1) and submit the
provided authentication information to the server.
·
The student will
submit screen shots of the Ethereal to prove that log-in information is
protected by IPSec.
2.
Telnet traffic:
·
The student will run
the Ethereal against one of the network interface cards.
·
The student will
connect to the Telnet server (as specified in project 1) and submit the provided
authentication information to the server.
·
The student will
submit screen shots of the Ethereal to prove that username and password can not
be read as in the project 1.
3.
FTP traffic:
·
The student will run the
Ethereal against one of the network interface cards.
·
The student will
connect to the FTP server (as specified in project 1) and submit the provided authentication
information to the FTP server.
·
The student will
submit screen shots of the Ethereal to show the testing username and password
can not be read.
d)
Problem
classification:
This experiment can be classified as a network assignment
and also as a study experiment.
e)
How it may be
implemented in the security lab:
This project requires a LAN environment and a network
server to provide WEB, TELNET and FTP services. This server can support both
non-secure and secure connection using IPSec. The client computer will be one
of the workstations in the D158 network. Each student will be given external hard
disk in order to install operating system and utilities. See section b (Tools
utilized) for relevant information.
f)
Level of difficulty:
Based on the level of difficulty, this experiment can be
classified as an experiment of intermediate difficulty.
g)
Grading criteria and
methods:
The grader checks the screen shots and the files of
captured network traffic to see if the student really succeeds to protect
network traffic using the IPSec protocol set.